
log files with google dorks

google dorks list and updated database

google hacking the hidden face of

google dorks an easy way of hacking

google hacking database ghdb google

google dorks for recon pentest tools

google dorks for penetration testing

google dorks hacking s new door by

exploit database redesign
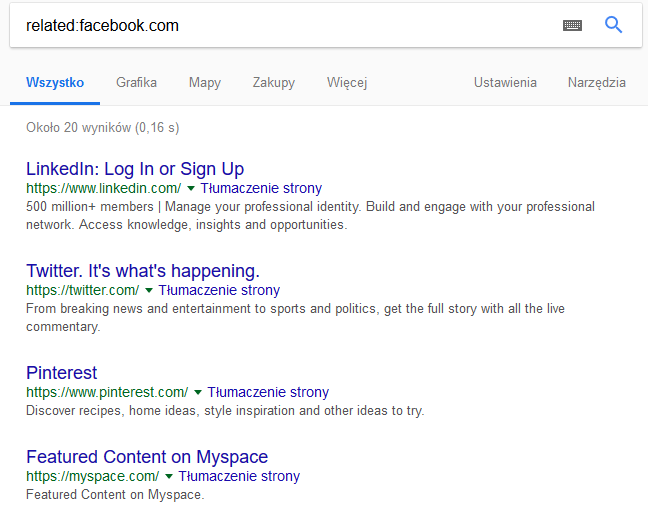
it infrastructure reconnaissance part

how they hack your website the

web dorking by google hacking database
how penetration testers use google
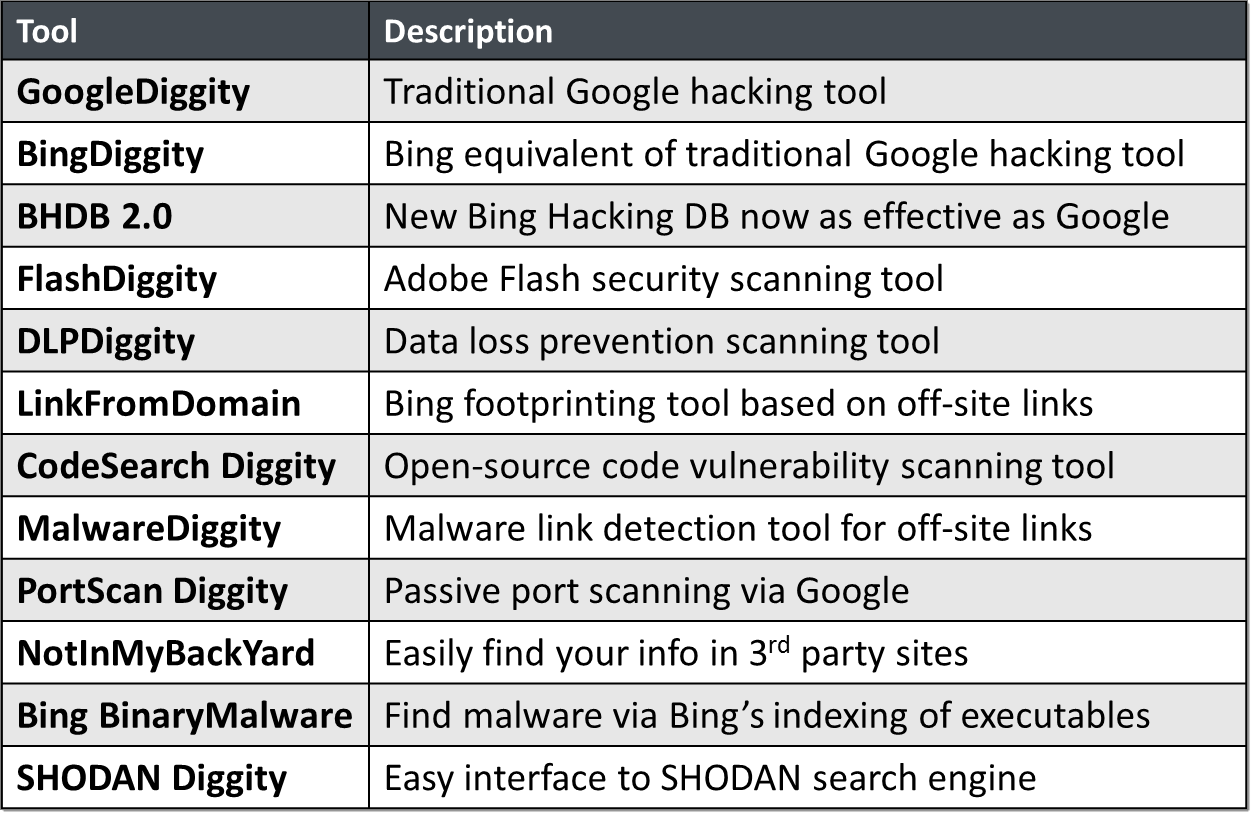
google hacking diggity project bishop fox

osint google hacking osintguru

google hack database automation tool

google hacking the hidden face of

search smarter by dorking the kit 1

thehackerstuff
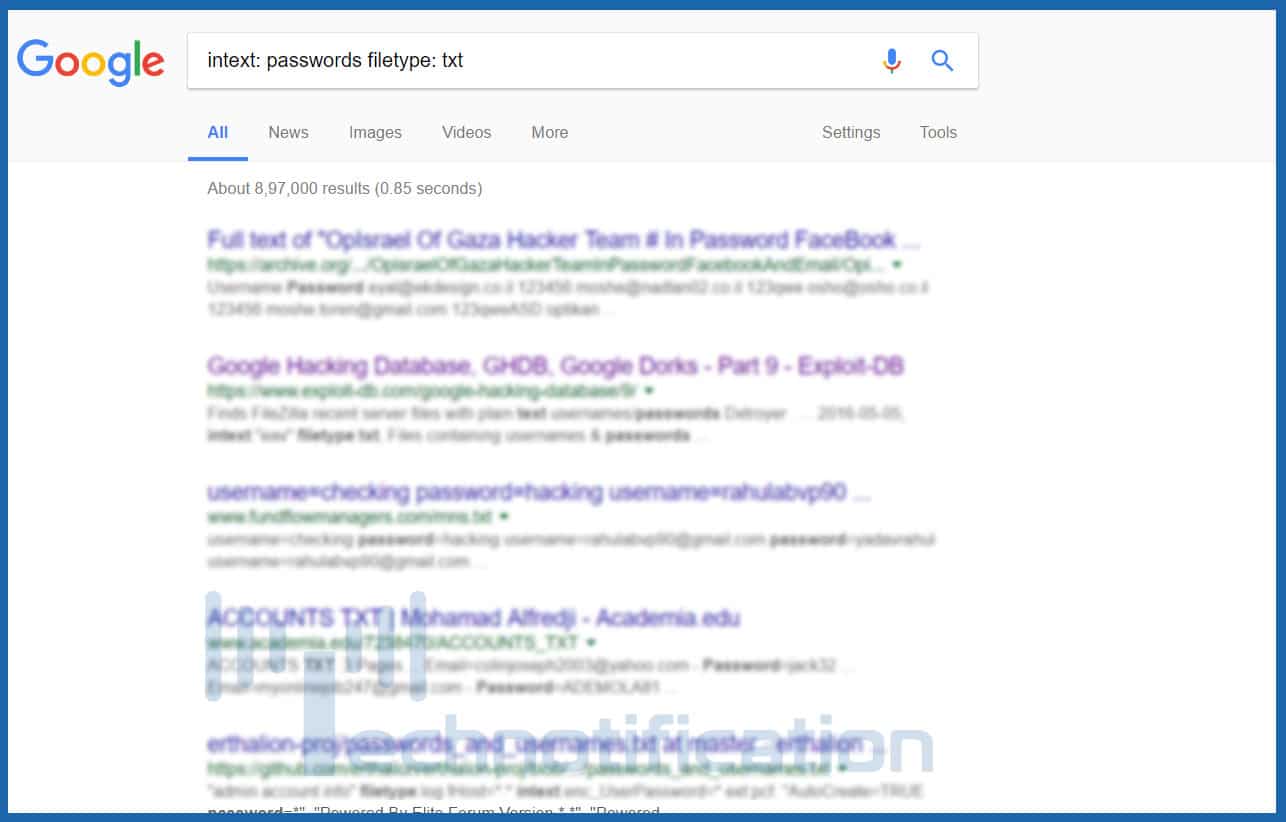
google dorks use google for hacking

google dorks
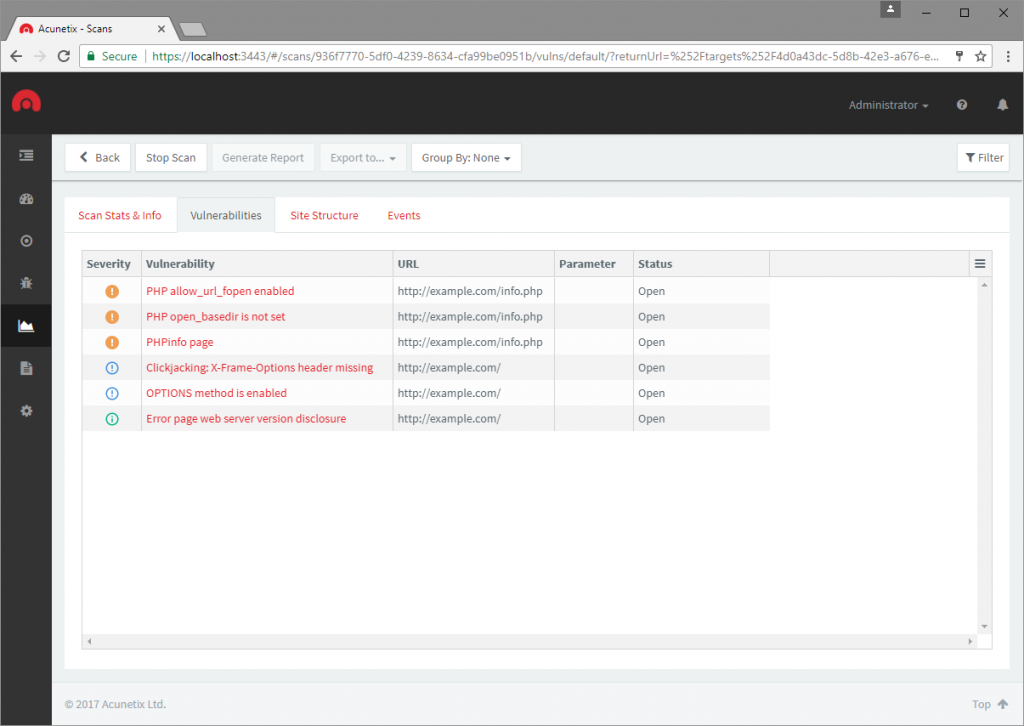
google hacking what is a google hack

google hacking database ghdb dgt

xmr 门罗币 monero
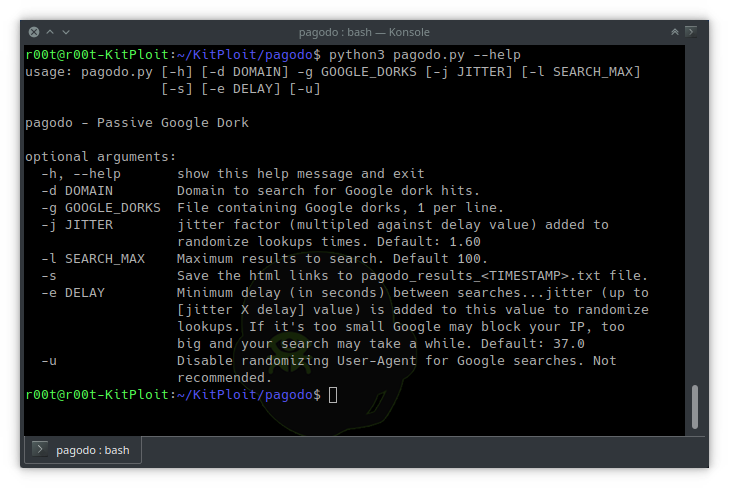
automate google hacking database

google hacking database ethical hacker

googledork hashtag on twitter

google hacking google code search to find vulnerabilities in software toolbox tech
You May Like